You’ve likely heard of FTP as a protocol for sharing files and information across the Internet. You may have also heard of SFTP, but what exactly is the difference?
Below, you’ll find details on the differences between FTP and SFTP, plus the reasons why SFTP is the most secure way to share sensitive information outside your organization. To make sure you’re maximizing your use of SFTP hosting, we’ve also included a comprehensive list of SFTP best practices.
Want to learn more about SFTP cloud server options, use of SFTP, SFTP cost, and general SFTP cloud solutions? Our team is always here to help. Contact us to chat with an SFTP expert.
What is the Difference Between FTP and SFTP?
The two terms look strikingly similar: FTP and SFTP. But the addition of that S at the beginning of the latter makes all the difference.
FTP stands for “file transfer protocol,” and FTP is the traditional protocol used for sharing files across the Internet. What does SFTP mean? SFTP stands for “SSH file transfer protocol,” with SSH representing “secure shell.” For this reason, SFTP is often shortened to “secure file transfer protocol.” And with good reason: The main reason to choose SFTP vs. FTP is for its heightened security.
The SSH encryption in SFTP is a type of algorithmic encryption that protects data during transfers. Basically, SSH encryption “scrambles data, making it indecipherable” to all but the sender and receiver of the file or files.
In short, SFTP uses a high level of encryption (indicated by the S), while FTP does not use any encryption. There is an SSL-encrypted option for FTP, but SFTP is a better standard to use. SFTP is superior because it only requires a single TCP/IP port to be opened (port 22).
When to Use SFTP
There are two basic reasons to choose SFTP over FTP for file transfers.
First and foremost, many organizations and government agencies are dealing with information so sensitive that it simply can’t be potentially exposed to unauthorized users (FTP has that risk because there is no encryption). For example, businesses may need to share employee-related information that includes social security numbers, legal names, home addresses, etc. Government agencies may need to share information related to a weapons system or advanced aircraft that it needs to protect against access by foreign countries. And multinational corporations may need to share proprietary information related to processes or products. In each case, the sensitivity of the information would necessitate the encryption available via SFTP.
The second reason to use SFTP is for compliance reasons. We’ll share more on this below, but your organization may need to work or do business with another organization that requires SFTP for file sharing. If you choose not to use SFTP, you won’t be able to take advantage of the business opportunity.
SFTP Security Best Practice Tips
As we draw closer to 2022, what are the current SFTP best practices? That is, if your organization wants to share files and sensitive information as securely as possible, how should it approach SFTP? Below, you’ll find 8 SFTP best practices to follow now and in the future.
1. IP Address Restrictions
The best SFTP services allow for IP address restrictions. To ensure the highest level of security when sharing files, you can restrict access to those files to only specific IP addresses. If anyone operating from a non-specified IP address attempts to access your files, they will be restricted.
2. Country Blockers
Country blockers allow you to use SFTP to share files with only users in specific locations. For example, imagine you’re doing business with the United States Army or Navy. The files you’re sharing need to be ITAR compliant. Not only does SFTP give you the higher level of encryption needed to keep the files secure, you can restrict access to the files only to users in the United States.
3. Firewalls
Leading SFTP service providers also use dedicated firewalls to prevent access by anyone outside your organization. These firewalls create a Virtual Private Data Center that allows for access only by specified users. Anyone trying to access the sensitive files must first pass through this firewall — but only approved users actually get through.
In a time of rampant cybercrime and hacking, dedicated firewalls provide the additional security you need to share sensitive data with confidence.
4. Intruder Detection
If someone from a non-approved IP address attempts to access your files, your cloud SFTP solution should immediately and automatically blacklist that IP address. This automated blacklisting will halt the hacking attempt. It will also add the IP address to a master blacklist that is shared across multiple SFTP servers.
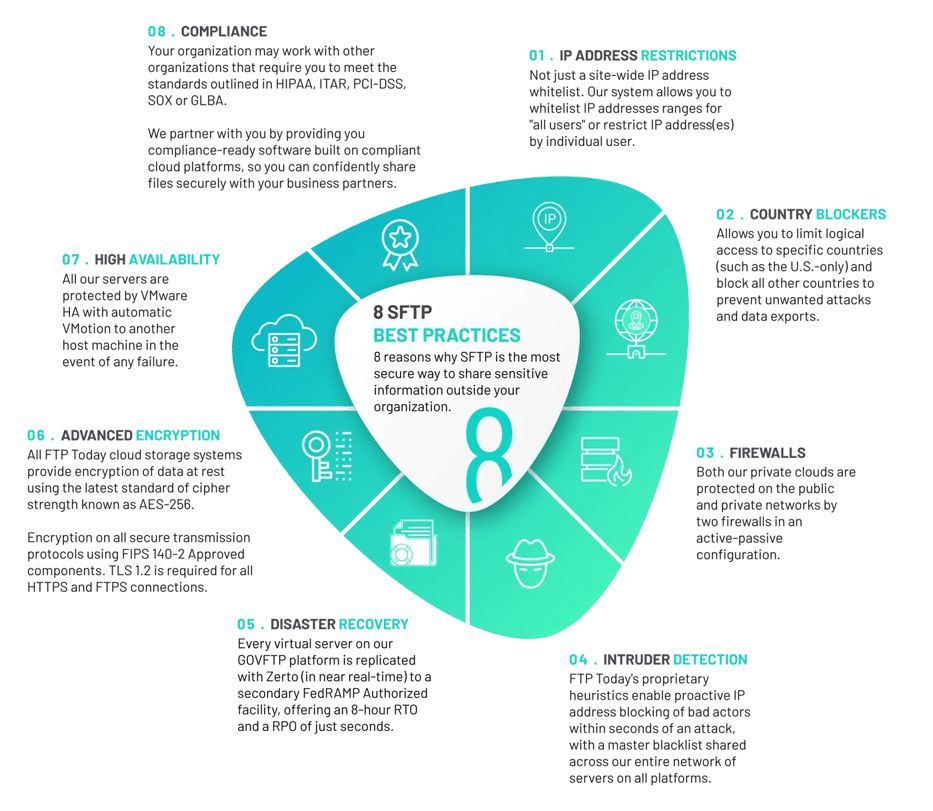
5. Disaster Recovery
Natural disasters and power outages can be threats to your data security. But, when you choose the right cloud SFTP provider, your sensitive data and files remain safe for two reasons.
First, high-quality SFTP providers use battery backups to keep servers working through power outages. Second, the best SFTP providers also backup data to servers in different locations. This means a server at risk during a natural disaster is fully backed up by a server in a completely different location.
Some organizations may attempt to buy and configure their own SFTP server on-premise. These organizations quickly find that owning an SFTP server is prohibitively expensive, both for setup and ongoing maintenance reasons. Organizations owning their own servers also struggle to backup files in different locations as needed during disasters. When you choose a leading cloud SFTP provider, you only pay a monthly fee to keep your data and files safe from the unexpected.
6. Advanced Encryption
SSH encryption keeps your files safe during transfer, and it also protects your login credentials. In addition to the SSH encryption both at login and during file transfer, the best SFTP providers configure servers to only accept connections at the highest levels of cipher strength.
SFTP users are handling data, information and files sensitive enough for the highest levels of security. If you want the highest levels of security in 2021, 2022 and beyond, you need the login and file transfer encryption provided by SSH encryption — as well as servers restricted to maximum cipher strength.
7. High Availability
So-called “high availability” is a way to configure SFTP servers to overcome common issues that can lead to downtime. SFTP high availability configurations redirect traffic to secondary servers when primary servers go down.
Things go wrong with SFTP server hardware, software and operating systems just like they do with other types of hardware, software and operating systems. With a high availability configuration, you experience zero downtime. Without a high availability setup, hours, minutes or even seconds of downtime could hold back your organization or even pose a risk to your data.
8. Compliance
As noted above, compliance is one of two common reasons that SFTP wins the FTP vs. SFTP debate — and the FTP vs. SFTP performance debate. Your organization may work with other organizations that require you to meet the standards outlined in HIPAA, ITAR, PCI-DSS, SOX or GLBA. If you’re doing business or otherwise working with these organizations, SFTP is the only way to go — and following SFTP best practices will be expected.
Scale Your Business with Sharetru
Most organizations don’t have the resources or manpower to buy, setup and maintain their own SFTP server. Sharetru is the leader among SFTP service providers. We offer cloud SFTP solutions that help you save — and that scale along with your business and its needs.
See our different cloud SFTP plans, and get in touch with our team for a demo of what our SFTP solutions can do for your organization.



